
Adept Security and Control
A secure environment for your most valuable information.
Protect your proprietary information from unwanted access by unauthorized users. Adept gives you the increased security, control, and traceability you need to have confidence in the availability, integrity, and confidentiality of your data.

Software development with a relentless focus on security.
Synergis takes data and application security seriously. Our design, development, and quality processes are built on industry best practices we’ve tailored to meet our customers’ requirements, and security is integral at every phase. Risk assessments are performed throughout design, development, quality assurance, and support to identify and address any potential issues.
Protect your data at rest, in transit, and in use.
Adept gives you increased security for your data in every state.
At rest - Adept supports OS level encryption solutions, such as Windows Bitlocker, which provides US Military top-secret grade, AES-256 (Advanced Encryption Standard) security. When documents are stored in a Bitlocker encrypted Adept Vault, the data is unreadable to unauthenticated users.
In transit - Data being transferred between servers and to and from authorized end users is accomplished using HTPPS with Transport Layer Security (TLS) encryption. This means passwords, financial data, and other critical information can’t be captured. In hosted environments, customer data is secured via VPN at data centers used by Synergis Technologies with HSTS enforced to protect cloud services against cookie hijacking and downgrade attacks.
In use - You control the data any given user can see, and you can mask any confidential data. Adept session time-outs help ensure data on a user’s screen can’t be accessed by unauthorized users without reauthentication.
Amidst the whole issue we had with the ransomware attack, if we didn't have that big project in Chicago completely contained within Adept, it probably would have sunk the project for us completely, and could have ruined the company.

Critical security integrations.
Adept integrates with Active Directory, simplifying user and group administration and automating platform on and offboarding. Adept’s Single-Sign On (SSO) support is compatible with common enterprise Identity Providers and enhances security and improves user experience while reducing your company’s attack surface. Secure Sockets Layer (SSL) transport ensures all data in transit is encrypted.
Emergency recovery.
A natural disaster or other crisis can impact even the most secure data centers. For this reason, data should be replicated to other data centers. Ensure business continuity with redundant data backups so your files and data can be restored quickly. In hosted Adept environments, data can be mirrored on two additional data centers, and documents may be stored at an alternate data center in the same region, at a data center in a different region, or replicated on in-house servers.
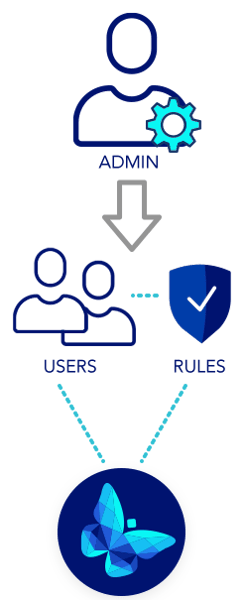
Granular access rights management.
Adept administrators control document access to ensure each user and group only has the access they need for any collection of documents. Determine who can view, print, markup, convert to PDF, create file relationships, edit metadata, edit protected fields, check in/out, move, rename, delete, and much more. Assign workflow administrators who can create workflows and determine who participates at each step.
Adept is our central engineering drawing repository for equipment across all of our plants. The system allows the engineers to enter, revise, and store the most recent documentation, while also having the ability to view past revisions. At the same time, it provides view and print capabilities of the most up-to-date prints to personnel in maintenance, operations and purchasing.
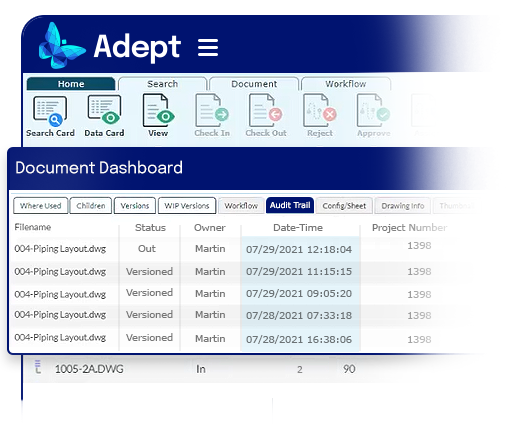
A searchable audit trail for extensive traceability.
Adept maintains an extensive, searchable audit trail for every document throughout its entire lifecycle, so you know who did what, when. Track down issues, gain insights, improve processes, streamline audits, and support litigation.
Smart document vaulting.
Adept secures your documents and the intellectual property they contain without sacrificing the intelligence of your existing folder structure and filenames. Unlike other solutions that scramble and render your files useless outside their proprietary system, Adept leaves them intact. Our vaulting system preserves the intelligence you’ve built over years. File links will continue to work, and if you decide to transition to another system in the future, your data won’t be locked up in a proprietary system.
Protect your intellectual property.
$6T
Cybercrime costs worldwide
$600B
Losses sustained by US companies from IP theft
1 in 5
US companies who have experienced IP theft



